Many times we are naively asked by end users, organizations, dealers and providers, about their security on the technological infrastructure level, the popular perception prompts them to protect themselves from external attacks, however, we must be as careful with attacks coming from the outside of our gateways as we should be with our own internal local area network, which use to be very risky as well, so to prevent attacks from your LAN (Local Area Network) is certainly a must.
House Cat? Sleeping with the enemy? With friends like that, who needs enemies?
This are just a few examples of popular phrases and jesting known around the world to say that the enemy or aggressor is nearest than we think; though, in this note, our ZARZA Engineers share some ways to avoid attacks from your Local Area Network, and some comments about it.
Is it a need to prevent attacks from my Local Area Network?
In many scenarios the answer is a straight: yes it is; however, without going further into your personal computer’s security, laptop or desktop, a very good advice is to learn the most important details of your LAN connection, the private IP configuration of it, which you may use on your own defense when proving what you’ve done, or not, from that connection, etc. All this in matters of being an end user, but in the scenario of an organization’s LAN, you should continue to read carefully, since you might be losing lots of money, but also to learn how to prevent attacks from your own Local Area Network.
Nowadays, envy and bad behaviors are so attached to society as they are to our closed job environments, that makes prevention of Attacks from you Local Area Network a daily basis topic.
If you share your Internet connection with others, you are certainly vulnerable.
So ZARZA Engineers, then what can I do?
First of all we have to start from the basics, having control of the most basic aspects and details, which we are going to explain in detail in just a moment, along with some other basic recommendations we always like to provide, which are always very helpful to prevent Attacks from Your Local Area Network:
- Mac Address – The address of your network card.
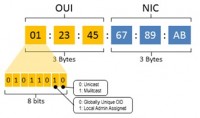 If your computer has a network card with an RJ-45 connector and/or Wireless access, your computer has at least 2 Mac (Media Access Control), which are basically the combination on a chain of 12 hexadecimal digits. This numbers are “unique” and auto-generated in every single computer. If the unit has bluetooth then it has one more Mac. Knowing your Mac Address lets you request your network administrator to do a DHCP or static reserve for the IP of your computer, so every time you go online the IP address will be exactly the same, avoiding that, in some logs, for example a co-worker on your office get the same IP address as yours, then doing any inappropriate action that will be associated to your computer. If you have a friendly network administrator, or if the configurations are being developed by a ZARZA Engineer, request as possible to have your IP address out of the DHCP pool, adding one more security step to prevent Attacks from Your Local Area Network.
If your computer has a network card with an RJ-45 connector and/or Wireless access, your computer has at least 2 Mac (Media Access Control), which are basically the combination on a chain of 12 hexadecimal digits. This numbers are “unique” and auto-generated in every single computer. If the unit has bluetooth then it has one more Mac. Knowing your Mac Address lets you request your network administrator to do a DHCP or static reserve for the IP of your computer, so every time you go online the IP address will be exactly the same, avoiding that, in some logs, for example a co-worker on your office get the same IP address as yours, then doing any inappropriate action that will be associated to your computer. If you have a friendly network administrator, or if the configurations are being developed by a ZARZA Engineer, request as possible to have your IP address out of the DHCP pool, adding one more security step to prevent Attacks from Your Local Area Network. - IP Address – Your Local ID in Your Local Network.
 Once you have a specific reserve, or an static configuration on your computer, you should take responsibility on the matter by checking from time to time the connection to your local network, to be sure you are using the same IP address as you should, preventing by doing so, Attacks from Your Local Area Network.
Once you have a specific reserve, or an static configuration on your computer, you should take responsibility on the matter by checking from time to time the connection to your local network, to be sure you are using the same IP address as you should, preventing by doing so, Attacks from Your Local Area Network.
Having a unique IP address, if your computer has an adequate reserve, you may be way less worried of someone else using your IP address either by accident, mistake, or in order to make you responsible of any incident. - vLan – Because not all is that easy…
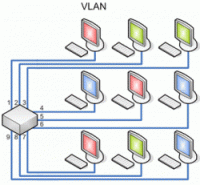 By just Googling a little, you will see how easy is to clone a Mac address, making others to be able to use your IP address even when taking the necessary precautions… This is due to the value of this tool for other type of configurations, but the bad guys know it very well. In regards to this, ZARZA Engineers recommend, as possible, to isolate the amount of workstations on the different vLans, which are little private networks inside of the same LAN. By doing so, if the workstations are all functioning at the same time and the attacker tries to clone the mac address while your computer is in usage, he will get an error, which under a well configured security could be detected by your network administrator, or by your personal trusted ZARZA Engineer.
By just Googling a little, you will see how easy is to clone a Mac address, making others to be able to use your IP address even when taking the necessary precautions… This is due to the value of this tool for other type of configurations, but the bad guys know it very well. In regards to this, ZARZA Engineers recommend, as possible, to isolate the amount of workstations on the different vLans, which are little private networks inside of the same LAN. By doing so, if the workstations are all functioning at the same time and the attacker tries to clone the mac address while your computer is in usage, he will get an error, which under a well configured security could be detected by your network administrator, or by your personal trusted ZARZA Engineer. - Private networks can also forbid mac address cloning by isolating the layer 2 and redistribute it on a separate net, protecting your computer from it.
Isn’t it just too paranoid following all the advices?
It depends on each scenario, however, we’ll tell you an anecdote of one of our ZARZA Engineers in Colombia, at the same time we want to encourage you to question yourself if it’s indeed just too paranoid, and to understand why it’s crucial to Prevent Attacks from Your Local Area Network.
[st_box title=”Not receiving his services payments.” type=”success”]Partner Engineers,
Today I was checking on a network-conflict issue (or that’s what the client reported), and I noticed that the connection they had previously established for the collection boxes section, was the same for the rest of the network. By doing some troubleshooting I detected the the Mac address cloning of the computer used to charge the credit cards, connected directly to the POS terminal, so the attacker was validating rooms using only the local validation (they never reached the POS terminal), so they were never really paying for the service, at least on the corresponding way. All this through the Public Wireless connection of the Hotel…
The client got really scared, since the money was never deposited into his bank account, but mysteriously the services were fully provided.
I isolated the problem by creating, from the client’s new ZARZA Private Node, a specific vLan for the computer used to process the charges, but I also activated sensors to detect from which segment of the network was the attack being generated, to be able to determine if the attacker was one of his customers, or someone closer to the hotel’s operations.
[/st_box]As you’ve read, that was a case when one of our new clients was, without noticing, being a victim of the lack of Prevention of his Local Area Network, costing him lots of money and potentially leading him to permanent millionaire losses, without him even noting it.
On this case, our ZARZA Engineer detected the problem, isolated it, but also provided an easy way to detect the source of the incident.
What else can I do to Prevent Attacks from My Local Area Network?
The most important is to trust on the professionals who guide you, preferably having Engineers as so. Sadly, nowadays the easy access to electronic devices and Information on the web, gets in risk clients who put all their trust in technicians and/or people who are just starting on the industry, people not trained enough, with no experience at all to help you Preventing Attacks from Your Local Area Network.
We know the value of your money and the importance it has for you, so we dedicate ourselves to keep is safe. That’s why our Engineers are the most experienced and professional on this Industry, so we can help you to Prevent Attacks from Your Local Area Network.
There are certain additional recommendations, as for example, if an efficient network administrator isn’t available, you may look to protect your connection yourself, by monitoring it with an independent router and a VPN. Consult with us by clicking here, or get in touch right now with your personal trusted ZARZA Engineer and, Prevent Attacks from Your Local Area Network.
Windows 2000/XP/Vista/7/8
- Windows 2000/XP/Vista/7/8
On the Windows environment, the MAC Address is known as the «physical address»
The easiest way to do it is by opening a command promt line («cmd» from Start>Run), then type the instruction: ipconfig /all, or you may also use the command: getmac. - UNIX, GNU/Linux and Mac OS X
On the *nix family environment, ((Mac Os X is based on UNIX), open a terminal and type the command: ifconfig -a.
This commands shows the interfaces followed by their respective MAC addresses on the ether epigraph. (Note: to execute “ifconfig” some distributions require root privileges: “sudo ifconfig -a”). By using the package iproute2, it’s possible to obtain the MAC addresses if all the ethernet cards: “ip link list”. In Mac OS X 10.5, 10.6 or 10.7, to know the Mac address you just have to go to System Preferences> Net, in the WI-FI field click Advanced. At the bottom of the new window you will find the correspondent Wifi address for your computer. - Android
Go to Settings, choose WI-FI configuration, then go to Menu>Advanced. Then you will see the MAC address of that device but also if it’s connected to a network and its current IP address. - Symbian
You may obtain the MAC address from the WLan and Bluetooth interfaces, to do so you have to type from the start screen the following codes: *#62209526# (meaning *#mac0wlan#) for Wlan, and *#2820# (meaning *#bta0#) for bluetooth. - Windows Mobile 6
You may obtain the MAC address of the WIFI device by going to the connections gester>Wifi>Configuration>WLAN Configuration>Connection status. Down below you will see the epigraph “MAC Address”. Windows Phone 8[edit]. You may check the MAC address by going to: Configuration>Information>More Information. It will show like this: MAC Address: xx-xx-xx-xx-xx-xx.
How to obtain the Mac Address on iOS devices ?
Go to Settings>General>Information. You will see the Wi-Fi Address and also the Bluetooth address.
 ZARZA We are Zarza, the prestigious firm behind major projects in information technology.
ZARZA We are Zarza, the prestigious firm behind major projects in information technology.


